Users could get impatient if a scenario arises on many web pages. Then, apps could display errors like HTTP 409.

What is HTTP 409?
HTTP 409 indicates that conflict with content’s present state prevented the user’s query processing.
It is a problem for search results as it frequently generates ambiguity. Moreover, it duplicates information. How the Content management system and the site communicate is also a concern.
The most common time for disagreements is in reply to a PUT query. It is when uploading a resource that is older than one that exists on the host. For instance, users can get this because of a versioning dispute.
The host must send a header with enough details to enable a client to identify the conflict’s origin.
Depending on the version control, the reply format would probably include data. These data would be relevant for integrating the difference.
What causes HTTP 409?
As its name implies, it is the consequence of a conflict within an HTTP query. As an aspect of examining this particular topic, we have to look at a lot of data.
There could be various causes for this.
- It could occur in the context of dynamic pages. Such as web pages that show data retrieved from databases or other resources.
- For instance, an asset may have an editing conflict due to many concurrent edits.
- It could occur since each requested item isn’t in the anticipated condition.
- Sometimes, naming your directory/documents with a restricted or banned name can fail.
- It could be caused when the host is in an overburdening state.
How to fix HTTP 409?
Because the reason might vary based on the circumstance, there isn’t a universal fix. Either users or a server is at fault.
Let’s go through them together, along with some suggested answers.
- Fix by regularly upgrading any operating system, including security updates. The updating option is easily accessible through “Settings” in Windows 10.
- You might fix it by conducting an SFC inspection. It scans all secured documents, and a cached copy will replace damaged ones. A solution list is here.
Launch the command prompt. Continue holding the “Windows icon” then hitting “X.” Next, open “Command-prompt.” And make sure to turn on the administrator privilege. Use the code below and hit Enter to begin the SFC assessment.
sfc /scannow
Our operating system would examine the file system. We encourage you to keep an eye on that console as you proceed.
One might proceed with the stages after the first evaluation. Its goal is to confirm and approve a specific resource.
You could restore a particular file, each at a time. Here it scans “ieframe.dll” and could correct an issue.
sfc /scanfile=c:\windows\system32\ieframe.dll
We could scan files using “/verify,” while no modifications done:
sfc /verifyfile=c:\windows\system32\ieframe.dll
After tasks/alerts are complete or presented, the command-line interface should end. Then after, restart the system.
- Run an anti-malware checkup on the machine. Search for malware/trojan and see if you can stop it. Infections may affect the way sites function in some instances.
- If using Java, then delete temporary online records. Select “Control panel” from “Start.” Then, find but double-click the “java” symbol. Underneath “Temporary Internet files,” pick “Settings.” Hit “Delete files.”
Also, check all items on the “Delete temporary” screen and hit “Ok.” Then hit “Ok” for all other windows when closing.
- It could be ModSecurity settings blocking CMS or WordPress scripts. A better way would be to fine-tune the “mod_security” to enable extra queries to route to a WordPress.
Here an illustration is Ten unsuccessful logins inside a Three-minute interval. Such rules would restrict access for said infringing Internet addresses lasting Five minutes.
To achieve it, update your customized Modsec client regulations. And insert the instructions below into the document.
This document is in “/usr/local/apache/conf/” for cPanel hosts. Here are some instances:
SecAction phase:1,nolog,pass,initcol:ip=%{REMOTE_ADDR},initcol:user=%{REMOTE_ADDR},id:5000134
<Locationmatch “/wp-login.php”>
# Configure brute force catching.
# Respond if the block flag is in place.
SecRule user:bf_block “@gt 0” “deny,status:401,log,id:5000135,msg:’Internet addresses closed for Five min, more than Ten logins in Three min.'”
# Configure Tracking. With successful logins, 302 redirects execute, and 200 state logins fail.
SecRule RESPONSE_STATUS “^302” “phase:5,t:none,nolog,pass,setvar:ip.bf_counter=0,id:5000136”
SecRule RESPONSE_STATUS “^200” “phase:5,chain,t:none,nolog,pass,setvar:ip.bf_counter=+1,deprecatevar:ip.bf_counter=1/180,id:5000137”
SecRule ip:bf_counter “@gt 10” “t:none,setvar:user.bf_block=1,expirevar:user.bf_block=300,setvar:ip.bf_counter=0”
</Locationmatch>
- You could be identifying a file library’s URL rather than the target document itself.
Trying like this could fix – “http://server_name/file_library_name/new_document_name.docx,” for example.
- Try changing the folder name of your site. For instance, alter from “group” to “groups.”
- It may also occur due to document size constraints for POST on a remote server. For instance, the Tomcat (Java host) has a default POST scale restriction of 2 Megabytes. Check the “maxPostSize” parameter to fix.
- Examine the URL. While attempting to create a directory “http://localhost:8080/directory/default/parent/newDirectory.” As “http://localhost:8080/directory/default/parent” might not exist.
Whenever placing the file inside the nested directory, ensure the directory exists. Do not forget about the trailing slash.
- Browsers could cache the query. You may deactivate this through the Chrome development interface. Or by including the header “{cache: ‘no-cache’}” inside the script.
- Fix via updating your platform’s URL to “HTTPS.” It is usually within “Settings” and then “General” in the dashboards. But then contact your provider for help diverting all “HTTP” communication to “HTTPS.”
- Try reactivating and reconnecting security add-ons such as “Jetpack.” Try toggling off/disabling security and third-party extensions on portals and internet browsers. These may purposely hinder connection.
How to avoid 409 error?
Organizations look at situations from several angles. Using the tips provided below may prevent alerts from occurring.
- The HTTP reply body collects details that the users might use to resolve the dispute. Thus, use user-friendly messages to avoid this.
You may well be able to specify a reply payload that a customer can use to solve the issue proactively. Or, at the very least, uniformly notify users what happened. For instance:
HTTP/1.1 409 Conflict
Content-Type: text/plain
You attempted to upload a document to a non-existent directory.
Make a directory and start trying!
- Avoid it by checking any plugin conflicts. For instance, use the ‘Health Check & Troubleshooting’ extension. And perform a conflict analysis without disrupting typical site users.
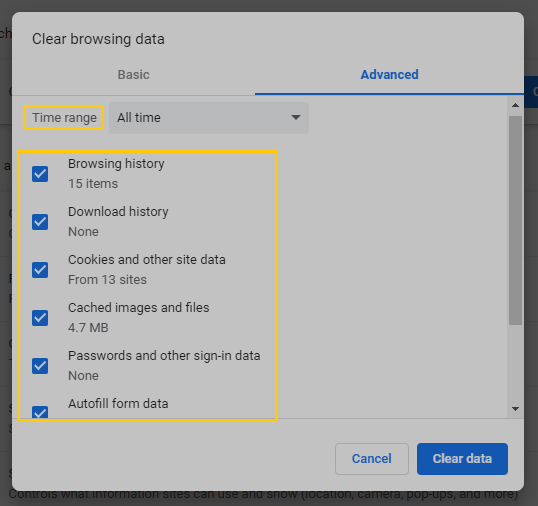
- The most effortless prevention may be to cut any unnecessary assets. For instance, we may drop a significant portion of our online activity. Throughout this step, on Windows PCs, use “Ctrl+Shift+Del.” Then after, choose “Advanced.”
As with intervals, pick “All Time” and check almost every item. Adding Caches and cookies to the list of things to erase is a must. To finish, tap “Clear.”
Conclusion
Developers use 409 code when the HTTP query is legitimate. It’s beneficial for APIs. But the hosts’ present condition prevented it from processing. For example, you’re writing a fresh blog post. Yet it references a removed classification.
Yet, the glitch doesn’t always specify which part of a query it cannot handle. As a byproduct, situations like this may be tricky.
The web application may remain stable with routine checkups and examinations. It eases your stress.
